Kubernetes Deployment Imagepullsecrets Example
For example in the case of docker only DockerConfig type secrets are honored. You can update your deployment YAML to utilise the above secretEstimated Reading Time.

How To Get Kubernetes Pulling From A Private Gitlab Container Registry
Node-RED Tekton Pipeline.

Kubernetes deployment imagepullsecrets example. Deploy to AKS pool. Kubectl apply -f -. A Deployment named nginx-deployment is created indicated by the metadataname field.
In other words a Deployment makes sure that a pod or homogeneous set of pods are always up and available. In this case you select a label that is defined in the Pod template app. The pipeline folder contains all the Tekton resources needed to create a pipline for a Node-RED deployment.
Verify by creating a Pod that uses a private image. Building Docker Image type. The secret names specified as inputs in the action are used to augment the input manifest files with imagePullSecrets values before deploying to.
NginxHowever more sophisticated selection. For example combining the previous examples you might enter. This document is a user introduction to Service Accounts and describes how service accounts behave in a cluster set up as recommended by the Kubernetes project.
If there are too many pods it will kill some. Because Secrets can be created independently of the Pods that use them there is less risk of the Secret. The specselector field defines how the Deployment finds which Pods to manage.
Kubernetes uses imagePullSecrets to authenticate to private container registris on a per Pod or per Namespace basis. If there are too few the Deployment will start more. A Secret is an object that contains a small amount of sensitive data such as a password a token or a key.
To do that yo need to create a secret with the credentials. The imagePullSecrets field in the configuration file specifies that Kubernetes should get the credentials from a Secret named regcred. List ImagePullSecrets is an optional list of references to secrets in the same namespace to use for pulling any of the images used by this PodSpec.
Echo SUCCESS EOF. In this example I will use azure container registry. During the deployment of an application to a Kubernetes cluster youll typically want one or more images to be pulled from a Docker registry.
NAME TYPE DATA AGE myregistrykey kubernetesiodockercfg 1 5d default-token-5gjfc kubernetesioservice-account-token 3 5d In this example the myregistrykey secret is available for use in the default namespace. In this post I will show you how you can use imagePullSecrets cluster-wide in Kubernetes. Very common issue with kubernetes Deployment.
Codefreshcf-deploy-kubernetesmaster commands-cf-deploy-kubernetes deploymentyml environment-email protected-KUBERNETES_NAMESPACEmy-namespace. Using the imagePullSecret in a deployment Add the imagePullSecrets parameter to the deployments YAML file. If specified these secrets will be passed to individual puller implementations for them to use.
This repo contains example Tekton scripts for deploying a node-RED pipeline on Kubernetes or OpenShift Container Platform. A service account provides an identity for processes that run in a Pod. The Deployment creates three replicated Pods indicated by the specreplicas field.
The k8s folder contains example deployment resources and Dockerfile that should be included in your node-RED project. Such information might otherwise be put in a Pod specification or in a container image. Using a Secret means that you dont need to include confidential data in your application code.
Kubernetes deployment imagepullsecrets example Pull an Image from a Private Registry You should avoid using the latest tag when deploying containers in that secret by adding an imagePullSecrets section to a Pod definition. Deploy to Kubernetes cluster with optional image version substitution. In this example.
For example a ConfigMap may be defined in the step with the name of my-app-settings and it will be created in the Kubernetes cluster with the name of my-app-setting-deployment-1234 where deployment-1234 is the ID of the Octopus deployment as a lower. The first step is to create the secret. Kubectl create secret docker-registry azure --docker-server myregistryazurecrio --docker-username --docker-password Using Deployment YAML.
Add an imagePullSecrets section to the manifest file that specifies the name of the Docker. Your cluster administrator may have customized the behavior in your cluster in which case this documentation may not apply. The other way is to add it to the default ServiceAccount in the namespace.
The tag spectemplatespecimagePullSecrets declares a reference to the cluster secret api-service-deployment-token created during the registration of the GitLab deploy token. Create a Pod that uses your Secret and verify that the Pod is running. The deployment describes the workshop layer in the cluster by providing information about how to obtain and maintain Docker images and containers.
Along with other deployment details. The valid format for pulling image from private repository in your Kubernetes Deployment file is. Containers Are A Critical Path.
By default the ConfigMap and Secret resources created by this step have unique names generated by appending the ID of the deployment. A Deployment ensures that a specified number of pod replicas are running at any one time. For example assume that the input Deployment manifest desired 30 replicas to be used for stable and that the following.
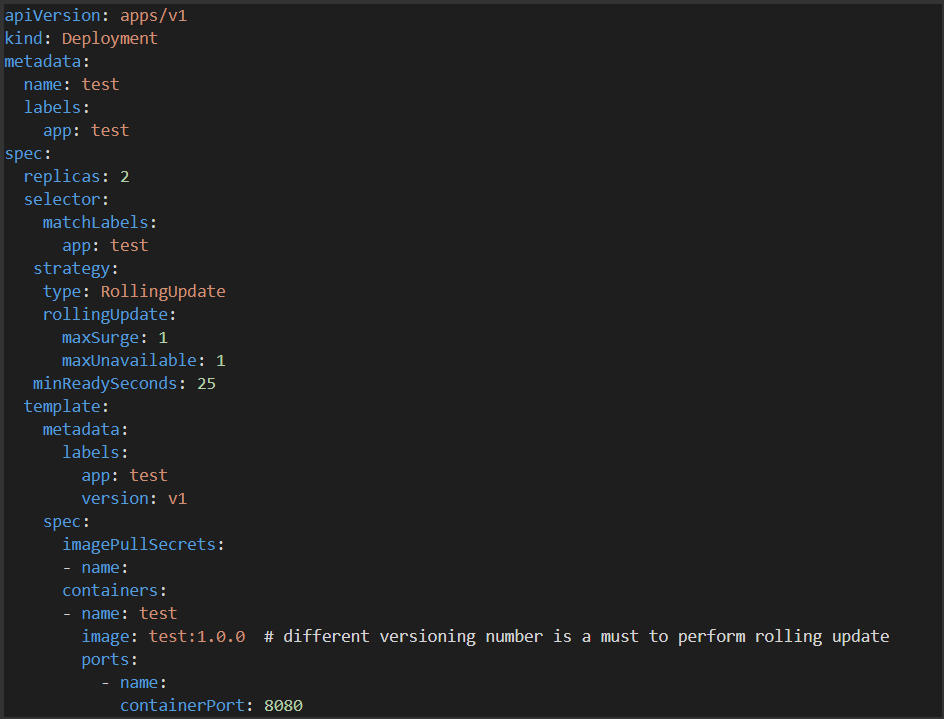
How To Setup Rolling Update In Kubernetes Deployments By Akila Rathnayake Medium
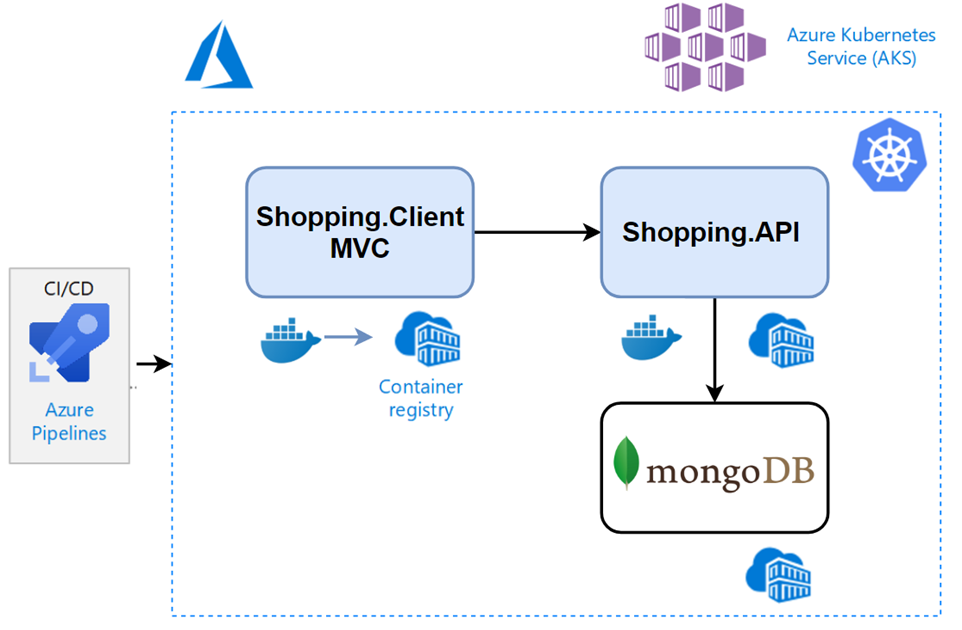
Deploy Microservices Into Cloud Azure Kubernetes Service Aks With Using Azure Container Registry Acr By Mehmet Ozkaya Aspnetrun Medium

Using A Private Docker Registry With Kubernetes By James Leavers Cloudhelix
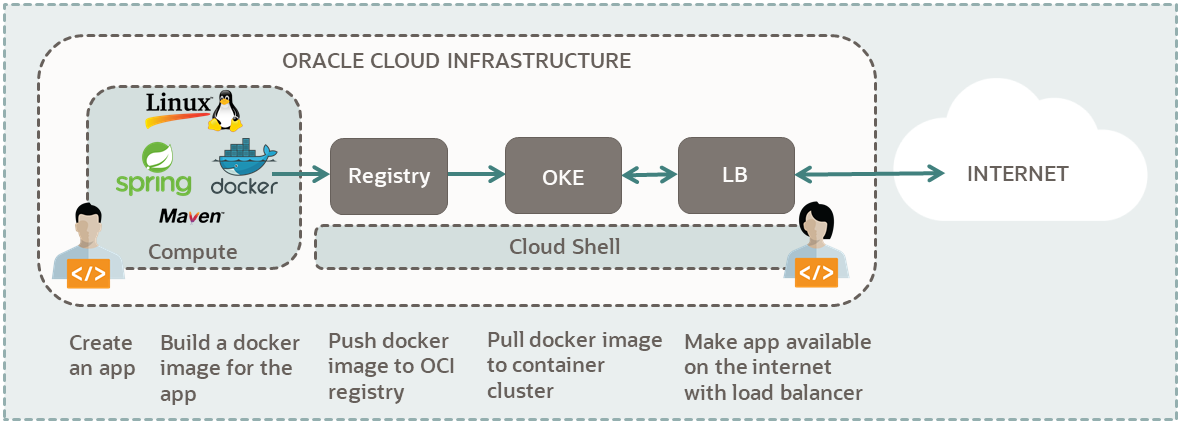
Kubernetes Using Cloud Shell Deploy A Spring Boot Application
Imagepullsecrets On A Deployment Not Been Propagated To Pods Issue 57801 Kubernetes Kubernetes Github
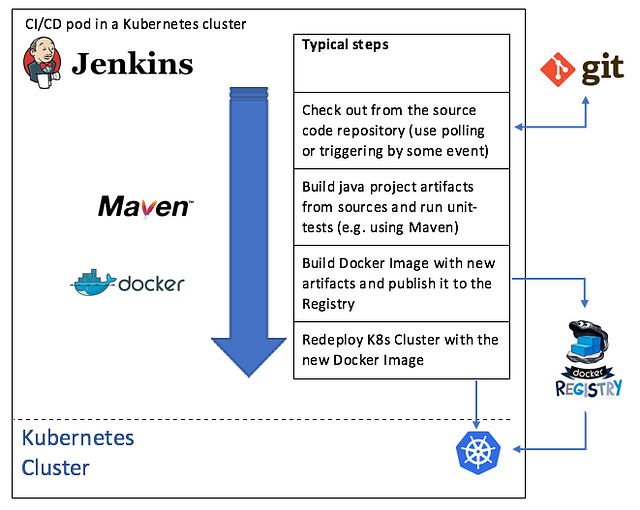
Jenkins And Kubernetes For Continuous Integration Continous Delivery

Deploy To A Kubernetes Cluster Octopus Deploy
Using Google Container Registry Gcr With Kubernetes
How To Use A Private Azure Container Registry With Kubernetes Thorsten Hans
Use Azure Container Registry With Azure Kubernetes Service Buchatech Com

Managing Secrets Deployment In Kubernetes Using Sealed Secrets Aws Open Source Blog
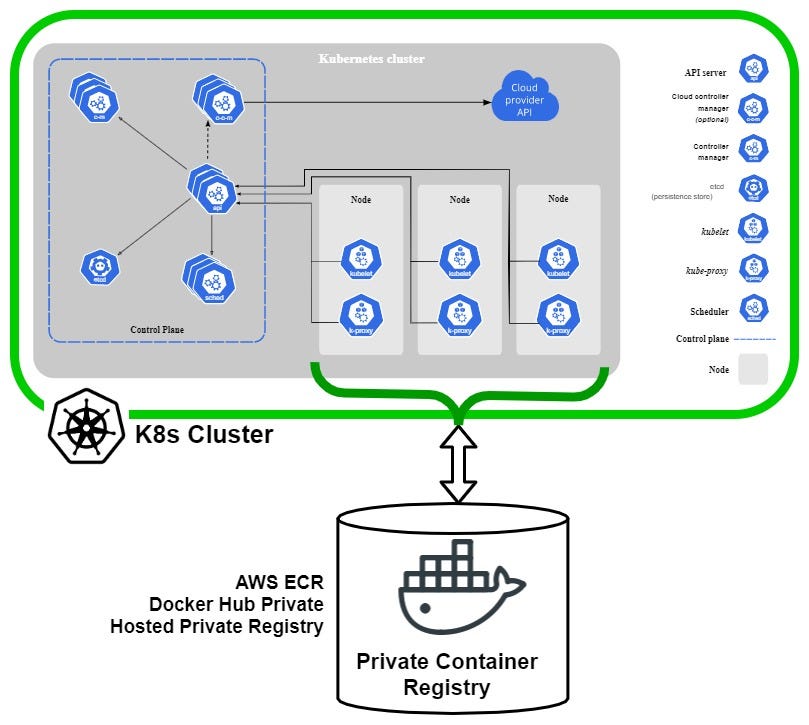
How To Use Images From A Private Container Registry For Kubernetes Aws Ecr Hosted Private Container Registry By Joe Blue Clarusway Medium
Pulling Images From Private Repo Using Imagepullsecrets Does Not Work Issue 817 Kubernetes Sigs Kind Github
Kubernetes Pull An Image From Private Ecr Registry Sergey Kryvets Blog
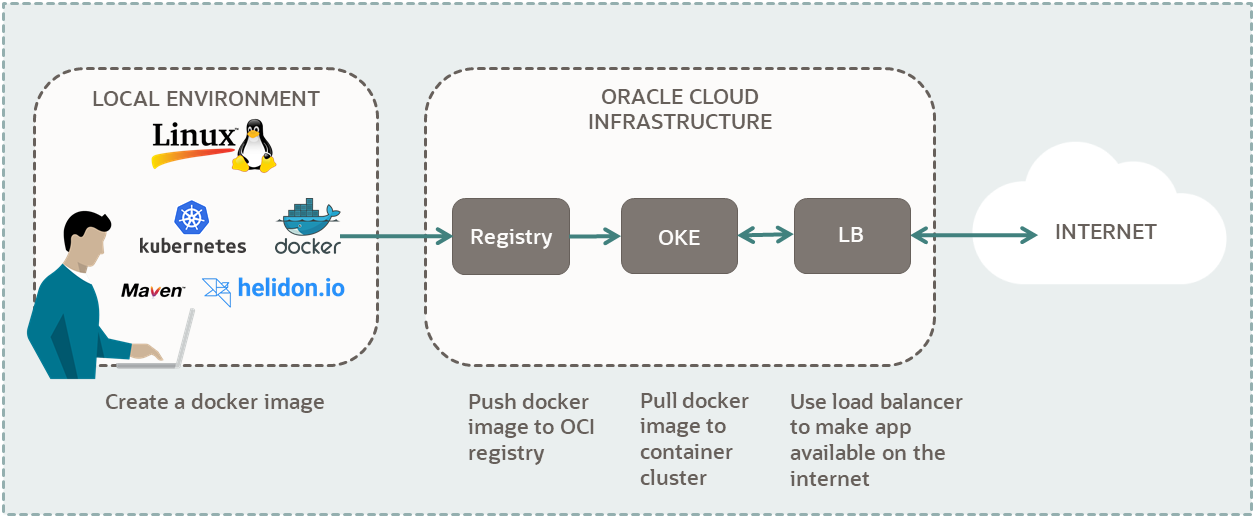
Kubernetes Deploy A Java Helidon Application

Set Up A Private Docker Registry With Tls On Kubernetes Civo Com
Kubectl Apply Removes All Imagepullsecrets When User Attempts To Remove Duplicate Secrets Issue 91629 Kubernetes Kubernetes Github


Post a Comment for "Kubernetes Deployment Imagepullsecrets Example"